The tireless efforts of various security researchers has surfaced critical, new information in this case. We are finally witnessing the missing link in how the compromised DLL is able to load the Cobalt Strike implant, and the threat actor’s intent.
Once again, this new evidence has proven just how sophisticated adversaries are becoming, and the extreme lengths they are willing to go through to evade detection. Now, more than ever these types of attacks are showing how important it is to use XDR and SIEM products for protection and threat hunting.
The below list of articles represent the most comprehensive threat intelligence we have reviewed on this subject. It is strongly recommended these articles are reviewed and your organisation checked against the new mitigation and forensic steps.
Over the holiday period, FireEye security published this post with additional technical details on the Sunburst attack. This analysis is verbose and shows additional defence evasion technique. This new information further proves the sophistication of this attack.
If you are using Azure Sentinel then new analytic rules are available to detect the post-breach behaviour. We recommend enabling these straightaway if you have not done so already.
If you are not running Azure Sentinel then we advise that you download and run the recently released Sparrow PowerShell script created by CISA’s Cloud Forensics Team here.
This tool will help detect possible compromised accounts and applications in the Azure/Microsoft 365 environment.
Transparity Security Analysts have been regularly reviewing the details regarding the Nation-State based attack against SolarWinds (known as either Sunburst or Solorigate). This attack is likely to affect your organisation in one way or another, so please take the time to review the information below.
Please note that Transparity do not use SolarWinds Orion; this post is for awareness only.
You may not be running SolarWinds Orion, so therefore will be currently unaffected. However, it is still recommended that you take the time to review the below information, as organisations you interact within your own supply chain may be using affected SolarWinds’ products. Please be diligent when opening emails and files that originated outside of your organisation.
For our customers utilising Transparity’s Datto RMM service, we are instigating an in-memory scan on all Windows-based devices to check for executables which show signs of infection. Customers will be contacted after the scan if there is any sign of infection.
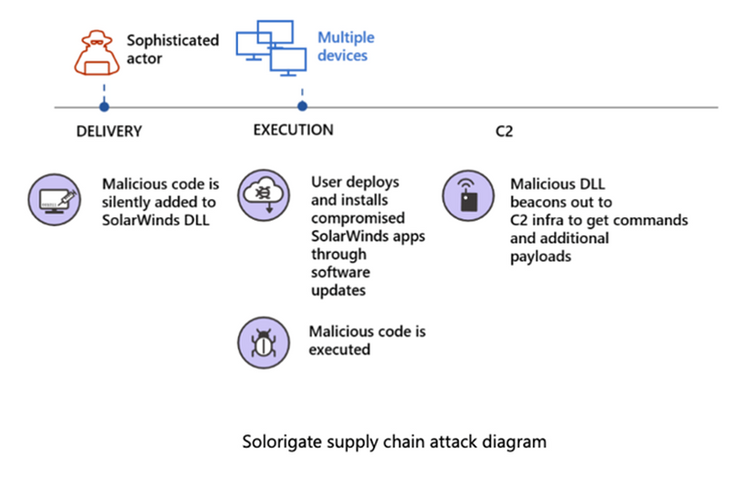
On 13th of December 2020, security firm FireEye discovered a supply chain breach in the SolarWinds Orion platform whilst investigating their own breach. This supply chain breach is one of the most sophisticated attacks ever executed. It has been performed by a Nation-State group of hackers, thought to originate from Russia. These attackers are highly motivated and agile. This attack needs to be taken very seriously. More details on the attack can be found below.
If you are concerned that you have been affected and would like to speak to our team of experts about remedial work, please email us at hello@transparity.com.