Introduction
In this blog series, we discuss Governance in Azure and how to ensure you have covered all aspects and thought about the most valuable areas for your business and the way you work. This blog looks at how Azure Tagging plays a significant part in establishing a strong Governance posture in your Azure subscriptions. Tags are similar to clothing tags, in that the tag would be used to identify a brand, colour, size, cost, record of demand, and ultimately its value to your business.
By utilising Tags in Azure, you can gain insights into your workloads, usage, associated costs, owner, and even orphaned resources.
When considering your Azure Tag strategy, it is sensible to consider the following:
- Applicable Objects – Tags can only be applied at a Resource Group or specific Resource level
- Naming Convention – A well-defined naming convention ensures easy-to-follow and uniform standards upon existing items and new deployments.
- Key Identifiers – Should you definine your workloads based on BC/DR, environment, function, owner, or a project?
- Automation – Will you be utilising some of Azure’s native services such as update management, automated shutdowns, or backups?
- Enforcement – You can use Azure Policy to automatically apply Tags on Resource Groups and Resources and for existing resources you can configure Remediation Tasks that will scan your subscription for already existing resources and apply a Tag directly to them.
- Cost Management – Your Azure subscriptions will integrate with Azure Cost Management and using specific Tags will help you identify resources in the GUI and help you forecast your spend.
Once you have defined your Tag Strategy, you should use Azure Policy to apply your Tags to ensure that all resources that support newly deployed Tags and/or create a remediation task to apply Tags to existing resources. There are multiple options within Azure Policy where you can apply Tags based on a Resource Group and subsequently the resources within can inherit the Tags.
Your Tag Strategy should be defined at the start of your Landing Zone design however these are common Tags that are frequently used as a baseline:
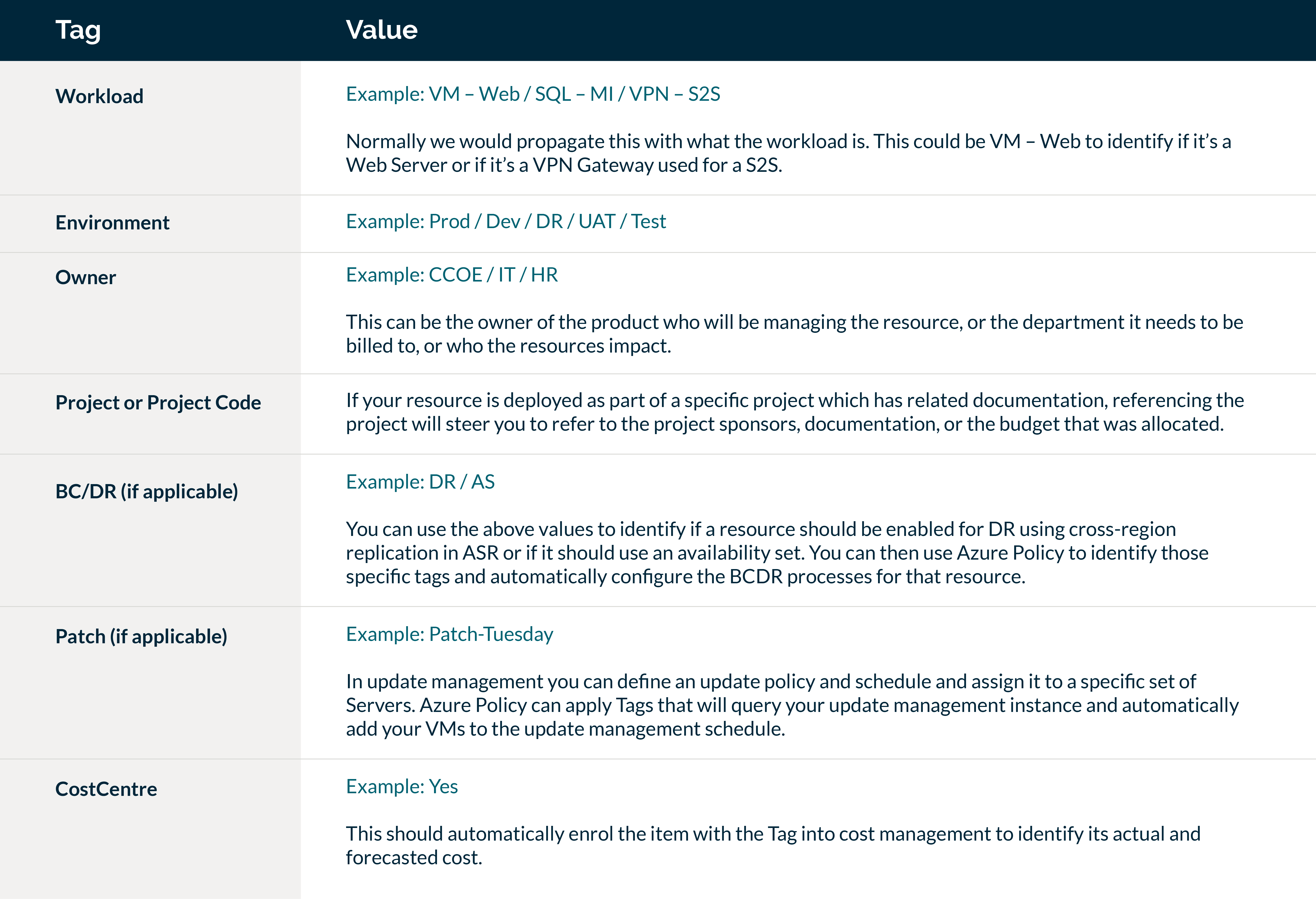
For fellow cloud engineers out there, here are the policies I have used in Azure to enforce Tags across Resource Groups and subsequent resources:
Policy 1: Add Tag to Resource Groups
In the table above there are 7 Tags we wish to apply. However you should consider this as 14 values altogether as you need to set both Tag name and value. These will be categorised together in Azure Policy as follows:
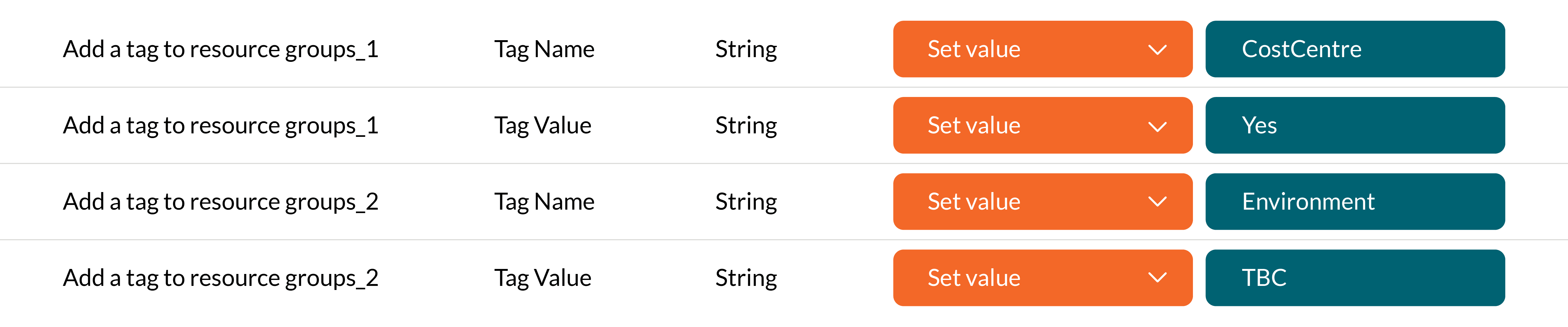
This will add the Tag to the Resource Group for CostCentre and its value being Yes – and for Environment and TBC as its value.
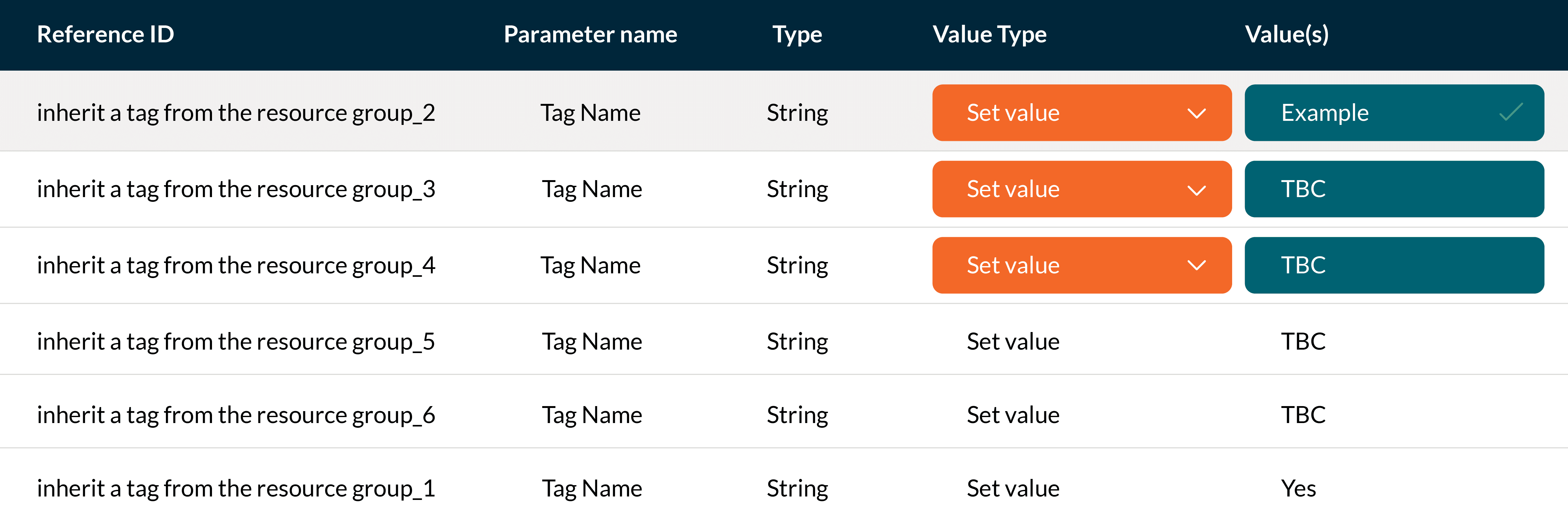
Policy 2: Inherit a Tag from the Resource Group
Once you defined what Tags you want to add to the Resource Groups you then need to configure the inheritance of the tags to ensure it is applied to the resources within the Resource Group.
The inherit tag policies will incorporate the same numbering that machines the numbers above and enforces the value against the Tag.
To summarise, Azure Tags provide us with the ability to categorise our Resources and allow us to use automation tools such as Azure Policy to fully automate standardisations across your Azure environment. By defining a robust and strict Tagging strategy, best practices can be implemented as standard and organisations can ensure their resources are embedded with cost optimisations and compliance within their subscriptions.
Four key takeaways
- Take the time to properly define what Tags are needed from an operational, technical, and financial point of view to ensure you can cross-reference your resources against your business resources/departments.
- Having a defined and strict naming convention will make it much easier to manage your solution and to identify costs.
- Once you have a design or understand what can be automated, ensure your Tags are aligned to this so you can utilise Azure Policy to set standards and compliance to ensure human errors are not a factor in future deployments.
- Use Azure Policy as a primary method for applying Tags and in general for uniformed deployments. This tool can save you a ton of time and unnecessary extra effort in house-tidying.
Future blogs in this series will cover the following:
- Azure Policy – An insight into how to define and enforce standards across your Azure subscriptions.
- RBAC Controls and PIM – We will explore RBAC in-depth, including built-in and custom roles, role assignments, and how to secure elevated permissions using Privileged Identity Management (PIM).
- Cost Management – Ensuring your solution is cost compliant is a key element of managing your ongoing Azure resources. We will provide an overview of how to budget, report and ultimately manage your costs in Azure.
- Azure Defender for Cloud – Exploring the differences between the Free and Paid versions of Defender and the value it can bring to your organisation.
- Auditing and Monitoring – Establishing effective auditing and monitoring practices is essential for governance and compliance. We will cover Azure’s auditing and monitoring capabilities, including Azure Monitor and Log Analytics, to help you proactively identify issues and ensure a well-protected environment.




